Table of Contents
Imagine if your entire college has only one big classroom and all the students from various departments have to attend their classes in the same room. Imagine how disturbing it is for students to concentrate on their own classes. What if this happens in a Network? How will you divide your network depending on the user’s needs?
Virtual LANs can be a solution for offering segmentation for a network.
What’s a Virtual LAN?
A Virtual LAN, or VLAN, is a logical segmentation of a switched network (a network that uses a switch). Unlike a LAN, which is a wired connection, this is a wireless connection, or, in fact, a logical collection of devices that works inside a LAN.
VLAN operates in Layer-2 (Data Link Layer) of the OSI reference model, meaning the devices are identified based on the MAC addresses which are stored on the switch’s CAM table / MAC address table, and the devices are logically segregated into groups.
You might be wondering about subnets, right? Yes, they do segment networks into smaller groups, but they operate on Layer-3 (Network Layer) and work on IP addresses.
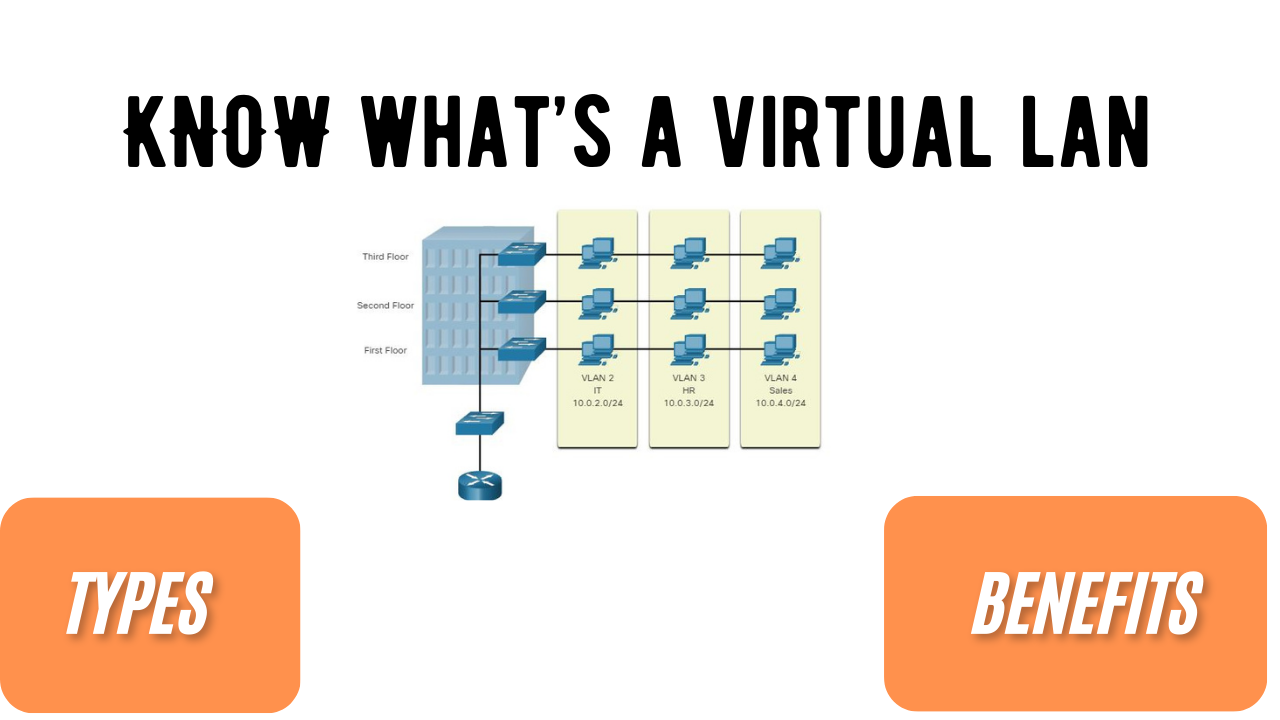
A network administrator can segment the network using VLANs based on their function, applications, or team. Each VLAN behaves as an independent network even if it shares the same network infrastructure with other VLANs.

Features of VLAN
There are certain conditions with VLANs when dealing with broadcast and multicast addresses when a message needs to be broadcasted, unicasted or multicasted within a VLAN the messages will only reach to the end device of the VLAN and not any other device on the network.
If a device of a particular VLAN needs to communicate with another device on a different VLAN on the same network it can only be done with the help of routing devices like routers and layer-3 switches as VLAN is treated as a separate network and communication between networks can happen only with Layer-3 protocols and devices.
Suppose we build a network with multiple subnets on the same switch and with no VLAN’s then the subnets are considered to be part of the same broadcast domain hence a broadcast message sent to one subnet is received by all other subnets. In case there’s a VLAN existing that divides these subnets then each subnet acts as an individual network and broadcast messages only go to the intended recipient.
Benefits of VLAN
There are several benefits of using VLAN in a network some of them are:
- Security: Only users in the same VLAN can communicate with each other, communications between VLANs must be explicitly allowed.
- Smaller Broadcast Domains: Dividing the network into VLANs can reduce the number of broadcast domains
- Increase efficiency: VLANs ease the setup of networks as devices with similar network requirements can be put under the same VLANs and can be named.
- Cost: VLANs don’t require purchasing additional network devices and efficiency can be improved with the use of the same available bandwidth and hardware.
Types of VLANs
Default VLAN:
In Cisco all VLANs are on VLAN1 by default unless explicitly defined to be on any other VLAN, hence all the ports are assigned to VLAN1, and it can neither be deleted or renamed. All the layer 2 control traffic is associated with VLAN1.
You can use “show vlan brief” command to see what all ports are assigned to the VLAN1.

Data VLAN
Data VLANs are configured to separate user-generated traffic (web browsing, email, file transfer etc), they are referred to as data VLANs because they specifically carry user-generated data. A network can have any number of data VLAN’s depending on the organisation requirements.
Voice and NEtwork management traffic are not allowed on Data VLAN.
Native VLAN
Whenever any user traffic is being sent to another switch then it must be tagged with a VLAN ID, when sharing this VLAN ID or what we call it as tagged traffic they are sent on a specific ports called trunk ports specially called as 802.1 Q trunk ports that carry 4 byte trunk header.
But in some cases these trunk ports may transfer untagged traffic generated by switches and this data is sent over by the native VLAN by the 802.1 Q trunk port..
Management VLAN
This Virtual LAN is specifically meant to handle network management traffic like HTTP, HTTPS, SSH, SNMP, TELNET etc. By default on Cisco switches the management VLAN is the default VLAN1.
Voice VLAN
A separate VLAN is needed to support Voice over IP (VoIP). VoIP traffic that requires VLANs to meet certain conditions:
- Assured bandwidth to ensure voice quality
- Transmission priority over other types of network traffic
- Ability to be routed around congested areas on the network
- Delay of less than 150 ms across the network
To meet such demanding requirements its important that the entire network is designed to support VoIP.
[…] remote EC2 connection with Python Netmiko. Virtual LAN: A Must-Know Concept for CCNA Success | 2025 Switching Concepts for CCNA certification “X-Forwarded-For”, exploit API […]