Before we get to SOAR we need to be aware of SIEM tools (Security Information and Event Management) that help in incident and threat detection. The SIEM tools operate based on predefined rules that you set when device, software, or network logs are ingested. Here the actions taken by the blue team are manual but when the SOAR system is added it makes defense even more effective.
Understanding Blue Team Environment
In a typical blue team environment that secure any application or network the following are the most common defenses that are implemented.
- Firewall: The firewall is responsible for blocking traffic based on pre-defined rules or reacting in a way it has been configured based on organisation’s threat landscape.
- IDPS : The Intrusion Detection and Prevention System’s primary responsibility is to find anamolies in traffic pattern and create alert, in some cases the IDPS can dynamically alter the firewall rules to prevent further attacks. Its important to note that the IDPS capabilities to dynamically manage the firewall or block attacks is limited.
- SIEM : The Security Information and Event Management tools such as Splunk ingest logs from IDPS and Firewalls, compare the incidents and generate alerts for the blue team to further investigate the incident.
- SOAR : Security Orchestration Automation and Respone a technology used to automate responses against an attack which are detected or confirmed by the layers (SIEM, IDPS) sitting above. The SOAR sits at the bottom of software based detection but above human detection and responses.
Basically a firewall prevents an attack, the IDPS detects an intrusion but also capable to prevent some, the SIEM tools take logs from firewall and IDPS to analyze and generate alerts under pre-defined scenarios and the SOAR is automating the initial response by the organisation for an attack.
Understanding SOAR
SOAR stands for “Security, Orchestration, Automation and Response”, and primarily aims at increasing coordination between security teams, security tools and systems (Orchestration), using tools to automate the responses. A typical SOAR tool contains the following important capabilities “threat and vulnerability management “, “incident response” and “security response automation”.
The SOARs ingest alert data from SIEMs, Firewalls, mailboxes etc and create alerts, The alerts trigger something called a playbook that automates the workflow and tasks as part of security response. Adding further to the automated workflows humans and machine learning assisted software can be further used to determine how future incidents are responded hence further diversifying the threat interception.
Sample SOAR Playbook:
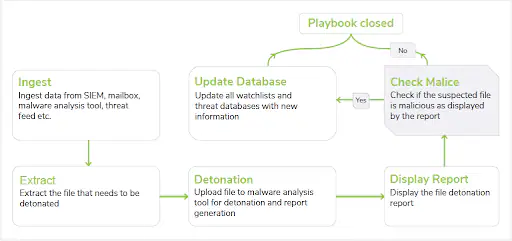
The above is a Palo-alto network playbook that determines how a playbook works. First, a log about a file is ingested which is suspected to be malicious. The log can be generated from an SIEM, mailbox or any malware analysis tool. Next, the file is extracted and further processed for detonation and report generation.
If the report says malicious the database is updated with new threat information and the playbook is closed. If the report doesn’t mention the file being malicious the file is directly closed.
This is one of many use-case scenarios. It can be used in detecting phishing links, malicious network traffic patterns, privilege escalation attacks, unauthorized access and much more as the threat landscape continues to expand rapidly.
Learning SOAR:
There are various resources available for free to learn the concepts of SOAR, there are official learning platforms from both Cisco and Splunk, the resources are mentioned below:
Splunk’s Free trail of their products : Free trails and Downloads
Splunk SOAR tutorial: Getting started with SOAR
Palo Alto Networks XSOAR: Cortex XSOAR 6.x Tutorials
Certification Courses for College : Udemy
Professional Certifications : Splunk SOAR Certified Automation Developer
READ OUR OTHER ARTICLES, BY CLICKING HERE
