Table of Contents
In the previous post, we discussed XSS and an example of JavaScript execution in an input parameter. That one was quite basic, and when browsers started input sanitization, that procedure may not always work. But today, let’s discuss 6 powerful techniques to check if a web application is vulnerable to XSS!
How to check for XSS?
Before we actually get into the techniques let us know how to identify a website if it is vulnerable to cross-site scripting or for now at least vulnerable to reflected XSS. The first and basic sign, that there is a potential vulnerability, is what happens when you manipulate the URL and how the DOM respond.
If you provide input in any available input field on a webpage and, upon inspecting the page using developer tools, you notice that your input is reflected within an HTML tag (such as <p>, <h1>, <u>, etc.) without proper sanitization or encoding, the webpage may be vulnerable to XSS attacks.
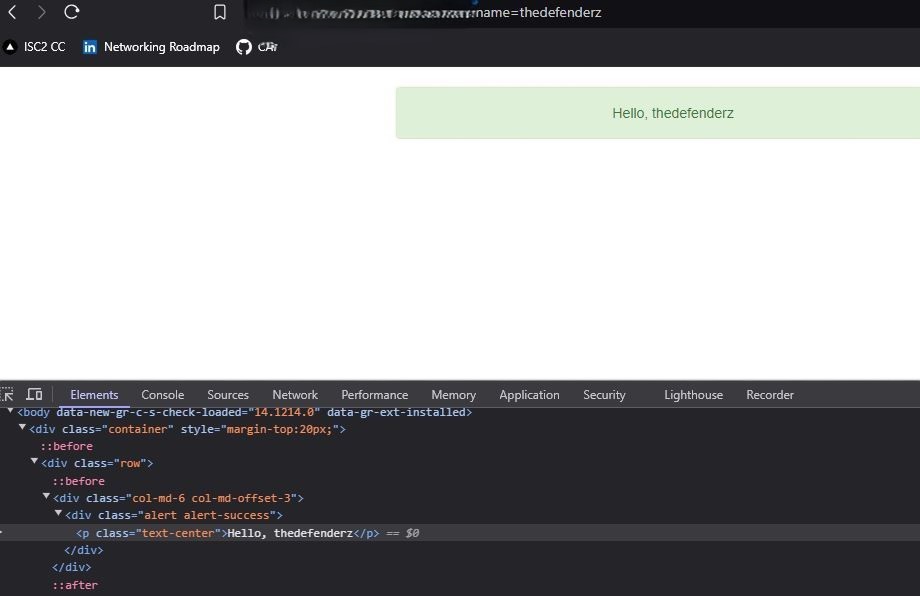
In the above example, we can observe that the input is taken within <p> </p> tags of HTML and we can manipulate the content within those specified tags. For Example
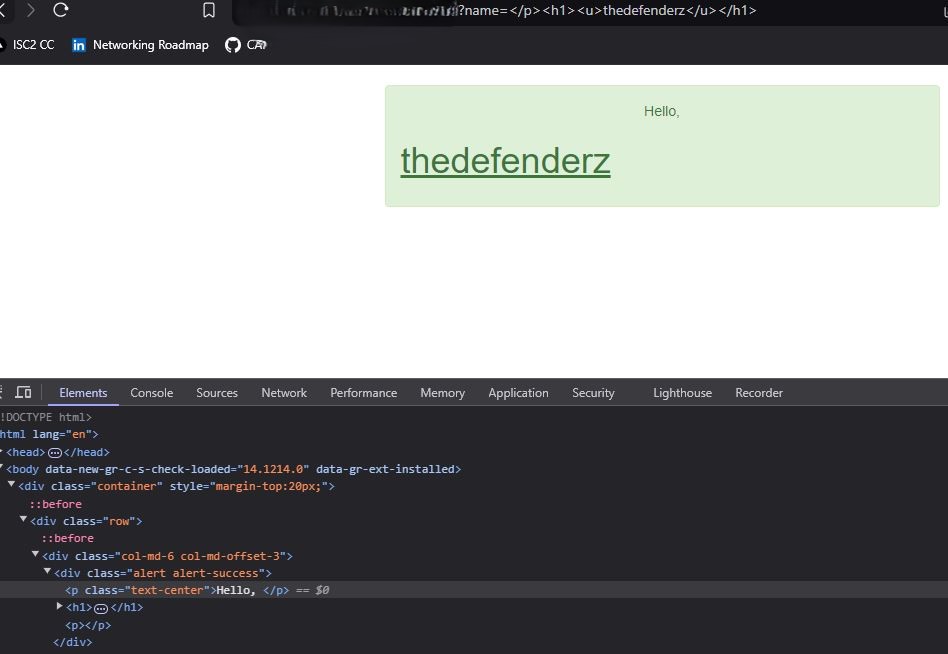
Here in the URL, we managed to close the “<p>” tag and add “<h1> and <u” tags and we can observe the input is not sanitized by the browser hence the changes are reflected on the webpage giving us the first signs of the existence of XSS vulnerability. Now let’s discuss about the techniques that we can use to test for the vulnerability.
Techniques for testing the existence of Cross-Site Scripting
There are various techniques for testing for its existence but the following is one of the effective ways to test for its existence, we have included the basic check using the <script> tag just for your quick revision but in most cases, it is sanitized by the browser or the application.
1. Using the <script> tag of HTML
The most basic check is discussed in our previous post, in the URL we can just use the <script> tag immediately after the “=” sign where it accepts input parameters.
https://xyz.com/?name=<script>alert(1)</script>Currently, you can find these vulnerabilities only in Lab environments but if you are lucky then you can get them in the real world.
2. Using data: URI in <script>
The other possibility is if your input gets sanitized because of any reason, or maybe you are using the “alert(1)” function directly within the <script> tag then we can try using the “data” URI available as an attribute for the <script> tag. You can use it by following the given syntax
https://xyz.com/?name=<script src=data:text/javascript,alert(1)></script>As there is nothing between the <script></script> tags the browser might think there is no javascript function being passed but in reality, we have asked the “src” attribute to consider the input data as “javascript”.
3. Using Event Handlers
Maybe when the browser is too smart or when the <script> tag is being sanitized by the browser or the application, we can use the JavaScript event handlers within any HTML tag. For Example
https://xyz.com/?name=<img src="xx" onmouseover="alert(1)"> Here we are trying to input an image then when we hover the mouse over the javascript event handler is triggered and executes the alert() function. We can also use the “onerror” handler of Javascript, the tag doesn’t matter until it is not being sanitized and we are able to include javascript functions inside them directly or indirectly.
4. Tricking the browser
In all of the above cases we have directly used any of the available HTML tags but now let us talk about a technique that tricks the browser into assuming that our input is just part of the URL. For that to happen we can use the “javascript:alert()” payload.
As “javascript:” is similar to URL contents like “http:” or “https:” it doesn’t treat the input as a threat but modern browsers have restrictions in using “javascript:alert()” directly in the URL.
But we can use it inside an HTML anchor tag which is different from all the above examples
https://xyz.com/?name=<a href=javascript:alert(1)>5. Using the <iframe> tag
The <iframe> tag of HTML allows you to open another HTML webpage or other content inside an existing webpage, because the <iframe> tag has a “src” attribute we can pass javascript functions into it.
https://xyz.com/?name=<iframe src = javascript:alert(1)>Here the “src” can hold any URL or contents and hence also JavaScript.
6. Using the <object> tag
The usage of the <object> tag is less common and hence is overlooked by the developers and may not be well scrutinized by browsers and developers and there is more focus on the <script> tag. Usually, the <object> tag is often used for embedding resources like PDF and its use for embedding Javascript is not often.
Unlike the <script> tag which is explicitly for Javascript, the </object> tag is not only for Javascript and hence is not discussed widely by researchers. You can test the payload with the following technique
https://xyz.com/?name=<object>data="data:text/html,<script>alert(1)</script>"</object>
With this we conclude this post, and here where the top 6 techniques to test for XSS vulnerabilities.
[…] 6 Powerful XSS Techniques That Will Blow Your Mind! […]